The Ultimate Guide To Protecting Your Business From Phishing Scams
February 27, 2024
Welcome to our guide on protecting your business against phishing scams. While companies understand the importance of bolstering cyber security, many may underestimate the prevalence of cybercrime today, particularly when it comes to Phishing.
Throughout this resource, we’ll delve into practical strategies for identifying phishing scams, fortifying your business’s defences, emphasising the critical role of employee training, and exploring the potential benefits of partnering with a cyber security firm.
Download your complimentary copy now to discover:
Don’t miss out on this valuable resource to strengthen your organisation’s security posture and protect against phishing scams. Download your free copy today!
Consider these eye-opening statistics:
With these statistics in mind, it’s clear that vigilance against phishing scams is paramount for safeguarding your business’s digital assets and reputation. Let’s explore how you can navigate this cyber threat landscape effectively.
Phishing scams represent a significant form of cybercrime, aimed at deceiving users to obtain sensitive information. Cybercriminals often masquerade as legitimate entities to perpetrate these attacks.
Employees in corporate settings are prime targets, as cybercriminals exploit social engineering tactics to trick them into compromising sensitive data. This can involve unwittingly downloading malicious files, clicking on infected links, or divulging private information.
In 2020, a whaling attack targeted the co-founder of the Australian hedge fund Levitas Capital. The co-founder received an email containing a counterfeit Zoom link. Upon clicking the link, malware infiltrated the hedge fund’s corporate network, resulting in the creation of fake invoices amounting to nearly $8.7 million.
Despite the actual financial losses from the attack being $800,000, it inflicted substantial damage to the hedge fund’s reputation. This led to the loss of their largest client and forced them to cease operations.
Between 2013 and 2015, Facebook and Google were duped out of $100 million in a prolonged phishing campaign. Exploiting their common vendor, Quanta, based in Taiwan, the perpetrator sent fake invoices impersonating Quanta, which both companies paid.
After uncovering the scam, legal action was taken in the US. The perpetrator was extradited from Lithuania. Through legal proceedings, Facebook and Google recovered $49.7 million of the stolen $100 million.
As malicious actors seek to exploit organisations, new types of phishing scams with varying techniques continue to emerge. Let’s explore the most common types of phishing attacks.
A whale phishing attack occurs when a fraudster impersonates a top executive within a company, aiming to obtain money or private information from another high-level executive within the same organisation.
For instance, a senior executive at your company might contact you regarding a financial crisis that requires your assistance. The fraudster may request login credentials or a wire transfer of funds to purportedly resolve the issue. This scenario illustrates a typical example of a whale phishing attack.
Vishing is a phishing scam where a malicious actor employs social engineering tactics to coax valuable information out of individuals over the phone.
For example, cybercriminals might impersonate personnel from a financial institution and call unsuspecting victims, soliciting their account information, PINs, or other credentials. They could also pose as vendors, suppliers, or partners to deceive individuals into divulging sensitive information or authorising payment for a counterfeit invoice.
Smishing involves the use of text messages, appearing to originate from a trusted source, to persuade recipients to provide financial rewards or access to exploitable information.
An instance of smishing could be receiving a text message purportedly from a reputable company or service provider, such as a bank or shipping carrier. The message typically alerts users about unauthorised activity or prompts them to verify account details.
BEC phishing scams primarily target accounting or finance personnel, with hackers aiming to deceive victims into transferring money from corporate accounts to their own.
Criminals begin by compromising financial employees’ email accounts and monitoring their activities to understand the organisation’s processes and payment procedures. They then send spoof emails impersonating top executives, instructing recipients to transfer funds into designated bank accounts.
In a clone phishing attack, scammers attempt to replicate legitimate branded emails previously received by the victim, while embedding a malicious link or attachment. Sometimes, the cloned email may include phrases like “resending” or “sending this again” to deceive the recipient into thinking it is from the original sender.
An example of clone phishing is receiving an email twice, with one originating from a slightly altered email address. For instance, you might receive two identical emails, one from “[email protected]“ and the other from “[email protected].”
HTTPS phishing involves cybercriminals tricking individuals into disclosing personal information via a malicious website. To lure victims to these sites, phishers conceal malicious links within emails, often disguising them as links to legitimate websites.
For instance, an HTTPS phishing scam might entail receiving an email instructing you to log into LinkedIn to secure your account. Although the email appears to be from LinkedIn support, it is actually a scam. Clicking the link directs you to a fake website designed to steal your login credentials.
Spear phishing is a targeted cybercrime tactic where attackers impersonate trusted sources to steal sensitive information, potentially leading to identity theft or other malicious activities. Unlike generic phishing, spear phishing focuses on specific individuals.
Both phishing and spear phishing leverage similar tools and tactics, aiming to manipulate recipients into taking action. They can utilise various channels like email or SMS.
However, spear phishing differs in its personalised approach and extensive research on targets. Unlike mass phishing campaigns, spear phishing’s tailored nature increases its success rate but limits the number of potential targets. These attacks are often executed by sophisticated hackers or state-sponsored entities, aiming to achieve specific objectives or target select organisations.
Recognising phishing attempts promptly is crucial for safeguarding your business’s reputation and data security. Yet, many individuals overestimate their ability to distinguish phishing emails from legitimate ones, as attackers often employ social engineering tactics to evoke emotions like fear, anxiety, or sympathy.
Here are the key indicators of phishing attacks to watch for:
Emails demanding immediate action under threat of consequences or loss of opportunity are often phishing attempts. Attackers exploit urgency to pressure recipients into hasty decisions before scrutinising the email for inconsistencies.
Phishing Emails often contain grammatical errors and spelling mistakes, unlike professionally crafted communications. Spell-checking tools commonly used by companies help identify legitimate emails, making linguistic errors a red flag.
Formal greetings or unfamiliar phrases inconsistent with usual office communication style should raise suspicion. Internal emails typically feature informal salutations, so deviations may indicate phishing.
Double check email details for inconsistencies. Hover over links to see where they go. Watch out for familiar names with strange domains or addresses – they might be trying to trick you.
Approach email attachments with caution, especially if they have unfamiliar extensions or are commonly associated with malware. Most file sharing now occurs via trusted platforms, so internal emails with attachments should be treated with scepticism.
Exercise caution with emails requesting login credentials, payment details, or other sensitive data, particularly if they come from unexpected or unfamiliar sources. Verify the legitimacy of login pages before inputting information, as attackers may create convincing replicas to deceive recipients.
Beware of emails promising rewards or incentives for clicking links or opening attachments, especially if the sender is unfamiliar or unsolicited. If an offer seems too good to be true, it’s likely a phishing attempt.
Reputable organisations don’t ask for personal data or sensitive credentials via email. Any email that appears to come from a supervisor, manager or colleague requesting sensitive information – especially phrased in urgent language – could be a phishing attempt.
Run through this simple 3-step checklist before responding to an email request:
To effectively safeguard your organisation against phishing attacks, it’s crucial to implement proactive measures and robust security protocols.
In safeguarding against phishing attacks, employee training plays a pivotal role in an organisation’s defence strategy. Here’s why it’s crucial:
To effectively combat phishing attacks, organisations should employ these strategies:
Identifying phishing links can be challenging due to their sophisticated mimicry of official notifications. If an employee falls victim, your company can mitigate the consequences by following these steps:
Avoid panic and assess the email for signs of malicious intent discussed earlier. Determine if data theft, malware installation, or network access has occurred.
Disconnect the affected device from the internet and all networks to prevent malware spread. Conduct a virus scan, delete detected malware, and reset compromised passwords.
Inform all employees about the phishing attempt, especially if it impersonated someone within the company. Notify customers or vendors if the sender disguised themselves as them to prevent further scams.
With a prompt and coordinated response, the impact of falling victim to a phishing scam can be minimised.
Phishing, posing as a pervasive threat to businesses, is meticulously orchestrated by cybercriminals to breach defences and compromise data integrity. Beyond the immediate financial losses, the aftermath of a successful attack encompasses profound reputational harm and operational chaos.
In the wake of such incidents, compromised data integrity, erosion of customer trust, productivity declines, and potential legal ramifications cast long shadows, underscoring the paramount importance of implementing robust cyber security measures to fortify against such pervasive threats.
It highlights the critical need for proactive strategies, including employee training, robust security protocols, and partnerships with reputable cyber security firms, to effectively mitigate the risks posed by phishing attacks.
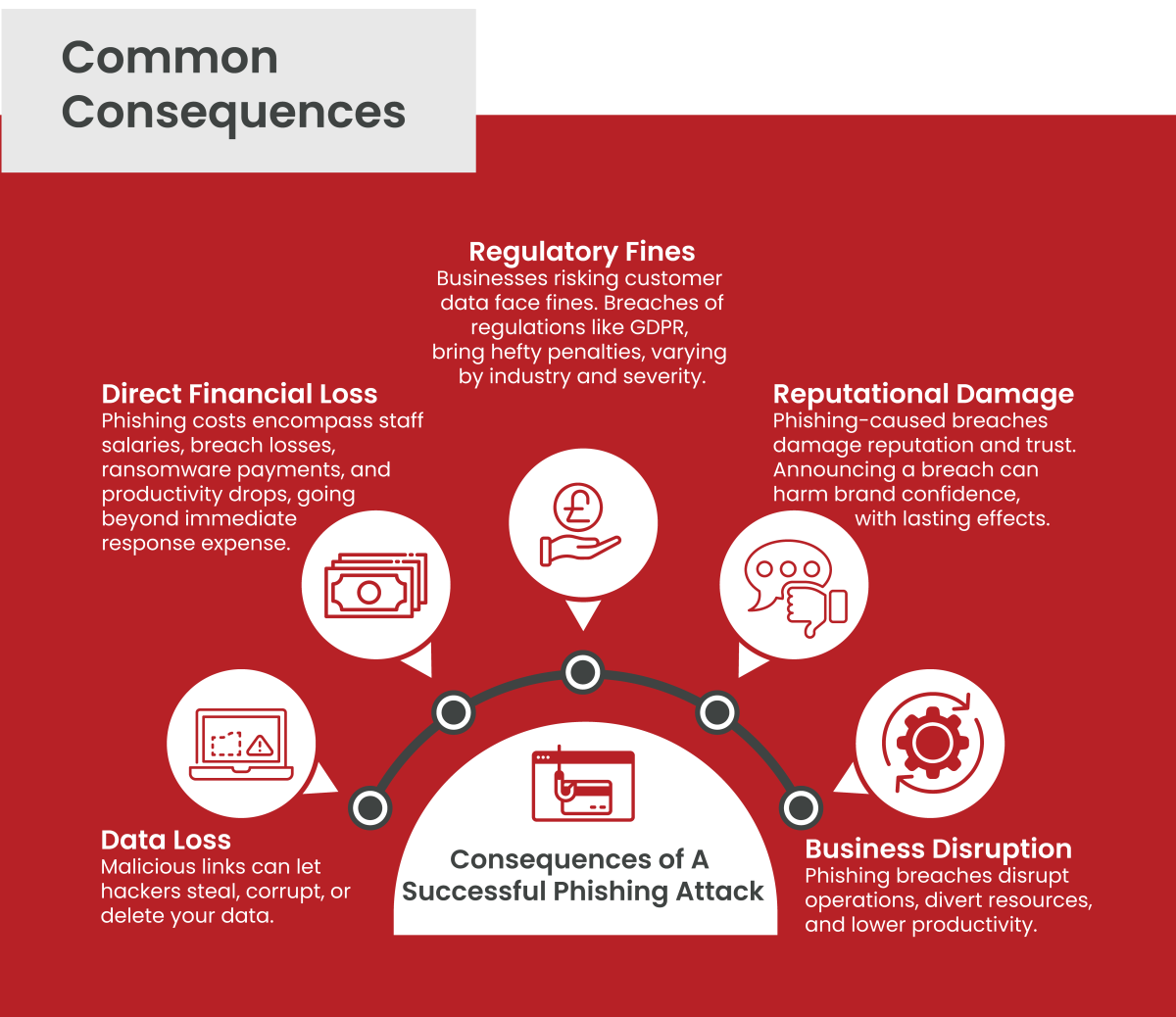
Clicking on malicious links can result in hackers gaining access to an organisation’s data and systems, leading to theft, corruption, or deletion—a significant consequence of phishing attacks.
The costs of phishing attacks extends beyond immediate response costs, encompassing salaries of dedicated IT and security staff, losses from data breaches, ransomware payments, and subsequent productivity declines.
Businesses failing to safeguard customer data face regulatory fines, particularly when sensitive information is exposed. Breaches of regulations like GDPR can result in hefty penalties, depending on the industry and breach severity.
Data breaches caused by phishing attacks tarnish a company’s reputation and erode public trust. The announcement of a breach can lead to a loss of confidence in the company’s brand, triggering long-term repercussions.
Phishing-induced data breaches disrupt business operations, diverting resources towards recovery efforts and investigation. Productivity declines as systems require reconfiguration and cleaning, impacting employee efficiency.
Protecting against phishing scams is increasingly challenging, particularly with the rise of sophisticated techniques. Many in-house IT teams lack the expertise and resources to address all potential threats effectively. A reputable cyber security firm can provide invaluable assistance in mitigating cyber threats and defending against phishing scams.
While this advice can help avoid a large proportion of phishing attacks, it’s advisable, if possible, to consult a cyber security expert to evaluate your existing security posture and recommend improvements based on the latest threat intelligence. Additionally, consider taking out insurance against cyber-attacks, offering both technical and financial support in the event of an attack.
And if, despite all precautions, your company falls prey to a cyber-attack, it’s crucial to report these incidents to the relevant authorities or local cybercrime unit.
Let us enhance your company’s cyber security and protect against phishing. Book a consultation today at [email protected] for tailored advice based on your company’s situation and see how you can minimise vulnerabilities.
Cyber security shouldn’t be a headache. Get clear and actionable insights delivered straight to your inbox. We make complex threats understandable, empowering you to make informed decisions and protect your business.
Call us +44 20 8126 8620
Email us [email protected]