Insider Threats in Cyber Security: Risks and Solutions
February 2, 2024
Cyber security often focuses on external hackers breaching organisational defences to access sensitive data. However, a growing concern is the threat from insiders. The rise in insider threats highlights a surge in incidents that many businesses are unprepared for. While advanced IT security software is essential, significant challenges remain, especially when the threat comes from within the organisation. This article aims to simplify the complexities of cyber security, providing clear solutions to mitigate insider threats effectively.
Insiders are becoming a significant threat to organisational cyber security. Recent statistics highlight a concerning trend that requires strategic attention. 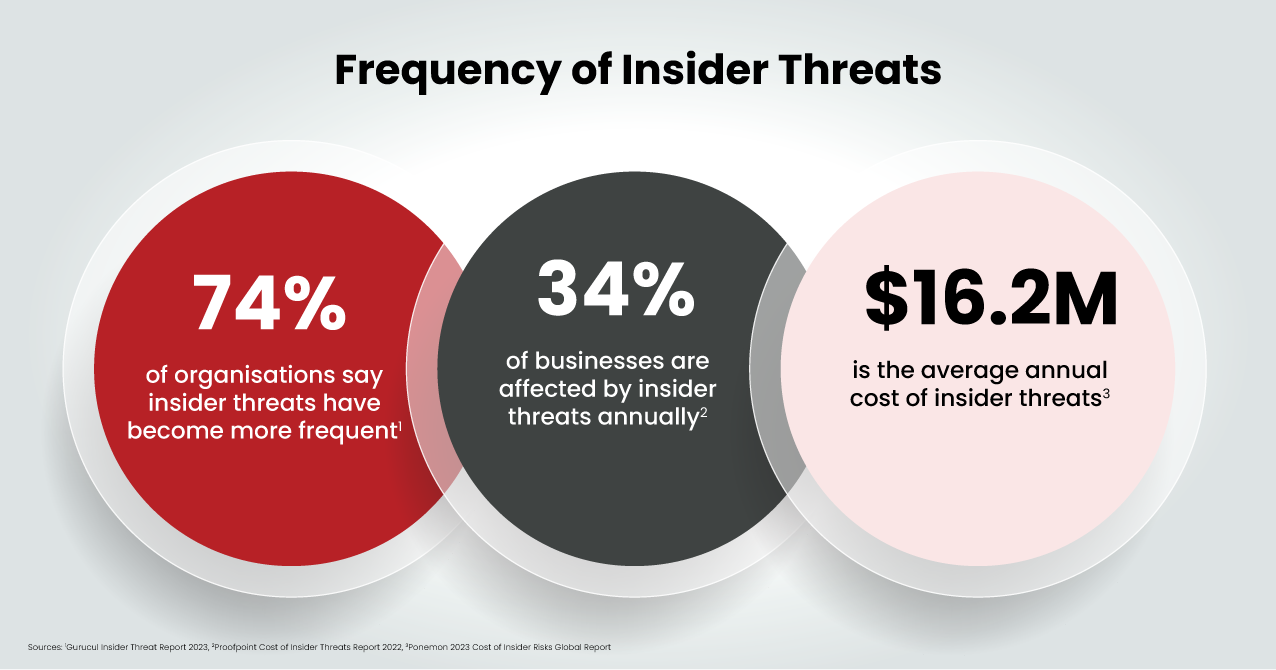
An insider is anyone with intimate knowledge of the business and its operations. Insider threats are significant security risks originating from within an organisation, driven by either negligence or deliberate actions. These threats, often having access to critical business information, pose a serious cyber risk that requires robust security measures.
Potential threat actors include:
Insider threats within an organisation manifest in two distinct forms:
Malicious insider threats are premeditated acts, often carried out by disgruntled or compromised current or former employees. Motivated by personal gain or revenge, these threats are frequently linked to criminal activities such as fraud, espionage, or data theft. Malicious insiders may act alone or in collaboration with external entities like cybercriminals, terrorist groups, or hostile governments. Common activities include:
Negligent insider threats arise from human error, carelessness, or manipulation, without malicious intent. Any individual within the organisation can inadvertently become a negligent insider by:
These incidents often coincide with broader cyberattacks involving malware or ransomware, highlighting the need to address unintentional vulnerabilities in organisational cyber security.
Understanding and differentiating between these two types of insider threats is crucial for organisations aiming to strengthen their defences against both intentional and inadvertent internal risks.
Detecting insider threats, whether due to malicious intent or negligence, is a complex challenge in cybersecurity. According to the Ponemon Institute, it takes an average of 86 days to contain an insider threat incident.
Two primary reasons contribute to the difficulty in detecting insider attacks:
Given the significant financial and reputational risks posed by insider threats, organisations must establish robust insider threat programmes specifically tailored to address this critical cyber security concern.
Internal attackers, whether intentional or inadvertent, are driven by diverse motives, each posing distinct risks to an organisation. Understanding these motivations provides valuable insights into potential vulnerabilities. The motivations can be categorised as follows:
Malicious insiders may seek financial exploitation through direct theft, embezzlement, or participation in illicit schemes. These actions impact the organisation’s financial stability and operational budgets, posing a significant threat to financial integrity.
Some insiders aim to inflict reputational damage by causing negative publicity, loss of trust, and harm to the brand image. The long-lasting consequences can affect relationships and market position, necessitating proactive measures to protect the organisation’s reputation.
Motivated by espionage, insiders may target intellectual property or trade secrets to gain a competitive advantage or sell to external entities. This results in the erosion of competitive edge, legal consequences, and compromised innovation, requiring robust measures to protect sensitive information.
Insiders with fraudulent motives may manipulate financial records, commit identity theft, or orchestrate schemes for personal gain. These actions lead to financial fraud, regulatory compliance violations, and legal repercussions, highlighting the need for vigilant monitoring and strong internal controls.
Insider threats pose real dangers to organisations of all sizes and industries, as illustrated by the following examples:
In 2023, Tesla fell victim to a data breach orchestrated by two former employees. The breach exposed sensitive personal data, including names, addresses, phone numbers, employment records, and social security numbers of over 75,000 current and former employees. Customer bank details, production secrets, and complaints about Tesla’s Full Self-Driving features were also disclosed. Despite legal actions against the culprits, the incident left an indelible mark on Tesla’s security reputation.
In May 2022, a Yahoo research scientist, Qian Sang, allegedly stole proprietary information about Yahoo’s AdLearn product just minutes after receiving a job offer from a competitor. Sang downloaded around 570,000 pages of Yahoo’s intellectual property to his personal devices, anticipating personal gain in his new role. Yahoo subsequently discovered the theft, prompting legal action against Sang for charges, including the theft of IP data, causing potential harm to the company’s exclusive control over trade secrets.
In August 2022, several Microsoft employees unintentionally exposed login credentials to the company’s GitHub infrastructure. This incident could have granted unauthorised access to Azure servers and other internal Microsoft systems. The potential repercussions included compromising Microsoft source code and exposing EU customer information, leading to a GDPR fine of up to €20 million. Cyber security firm spiderSilk detected the leaked credentials, enabling Microsoft to take corrective measures and prevent unauthorised access to sensitive data.
Recognising and understanding insider threat indicators is crucial for preventing potential harm. Here are the top five indicators that organisations should monitor, each requiring specific detection strategies.
Understanding and actively monitoring these indicators not only strengthens an organisation’s security posture but also contributes to a proactive and effective insider threat detection and prevention strategy. Vigilance in these areas is essential for maintaining the integrity and resilience of cyber security defences against insider threats.
Effectively countering insider threats requires a multifaceted approach that combines human insights with innovative technological solutions. This comprehensive strategy includes both human and technology elements for robust insider threat detection:
By combining human insights with advanced technological solutions, organisations can create a comprehensive insider threat detection strategy. This not only strengthens defences against potential threats but also ensures a dynamic and adaptive approach to evolving insider risks.
To protect against insider breaches, proactive policies and persistent efforts are essential. The following strategies form a comprehensive framework for preventing insider threats:
Thorough screening procedures are the first line of defence. Conducting in-depth background checks, including criminal and financial histories, helps identify potential vulnerabilities before granting access to sensitive data. Continuous vetting, especially for high-security roles, ensures ongoing suitability and reduces the risk of insider threats.
Implement stringent audit policies and encourage a culture of communication to minimise insider threat risks. Policies requiring comprehensive reviews and signoffs for employee actions help detect and rectify mistakes or negligence. Open communication enhances awareness of major projects and potential insider threats, facilitating early intervention.
Adopting Role-Based Access Control (RBAC) policies is crucial for restricting employee access based on specific job responsibilities. This aligns with the zero-trust model, which assumes all employees could pose insider threats. Limiting access according to job roles mitigates risks and forms a critical defence against unauthorised activities.
Periodic reviews and audits of security policies are essential to stay ahead of evolving insider threat scenarios. Regular evaluations ensure that policies, including employee screening procedures, incident response plans, and vulnerability tests, remain current and effective. Swift response plans are indispensable for countering insider threats, ensuring immediate mitigation and preventing unauthorised access or sabotage.
Implementing robust data encryption measures is a strong defence against insider threats attempting to exploit unprotected data. Encryption strategies for critical assets prevent unauthorised viewing or transmission of sensitive information. Secure key management practices further enhance the integrity of encrypted data, contributing to a proactive defence against insider threats.
The pervasive and evolving nature of insider threats highlights the critical need for a proactive and comprehensive approach to cyber security. Organisations must understand the motives and risk characteristics driving insider threats and implement effective detection and prevention strategies.
Effective insider threat management requires a blend of human insights and advanced technological solutions. By conducting thorough employee screenings, performing regular security audits, enforcing role-based access control, and implementing robust data encryption, businesses can significantly reduce their vulnerability to insider threats.
Navigating the complexities of cyber security and countering insider threats requires specialised expertise. Our dedicated team simplifies this process by assessing your organisation’s vulnerabilities, developing tailored prevention strategies, and deploying innovative technologies. Book a discovery call to find out how we can support you.
Cyber security shouldn’t be a headache. Get clear and actionable insights delivered straight to your inbox. We make complex threats understandable, empowering you to make informed decisions and protect your business.
Call us +44 20 8126 8620
Email us [email protected]