Zero Trust Network Access (ZTNA) for Enhanced Private Equity Security
October 27, 2023
Private equity firms are navigating a significant transformation, moving from legacy data centres to cloud-based and software-as-a-service (SaaS) solutions. Central to this shift is the adoption of Zero Trust Network Access (ZTNA), simplifying the complexities of cyber security.
In the face of escalating ransomware and cyberattack threats, ZTNA offers a ground breaking approach that transcends traditional perimeter-based defences. Its scalability and agility perfectly suit the financial sector, providing robust protection for a dispersed workforce.
The urgency of this transformation is highlighted by a recent CIPD report, which found that 2 million UK workers resigned last year, primarily due to a lack of flexible working options. Additionally, 71% of employees now prefer flexible working models over traditional office setups.
As hybrid working and cloud adoption rise, evolving access management to critical enterprise applications, regardless of their hosting location, is crucial. Zero trust provides an innovative security and access framework that seamlessly connects users to enterprise resources while enhancing the user experience.
The Zero Trust security framework is built on the core principle of “never trust, always verify.” It challenges the traditional notion of inherent trust and emphasises the need for robust, continuous authentication and authorisation for both devices and users. Within this broader framework, Zero Trust Network Access (ZTNA) stands out as a set of technologies designed to provide secure remote access to applications and services, adhering to strict access control policies.
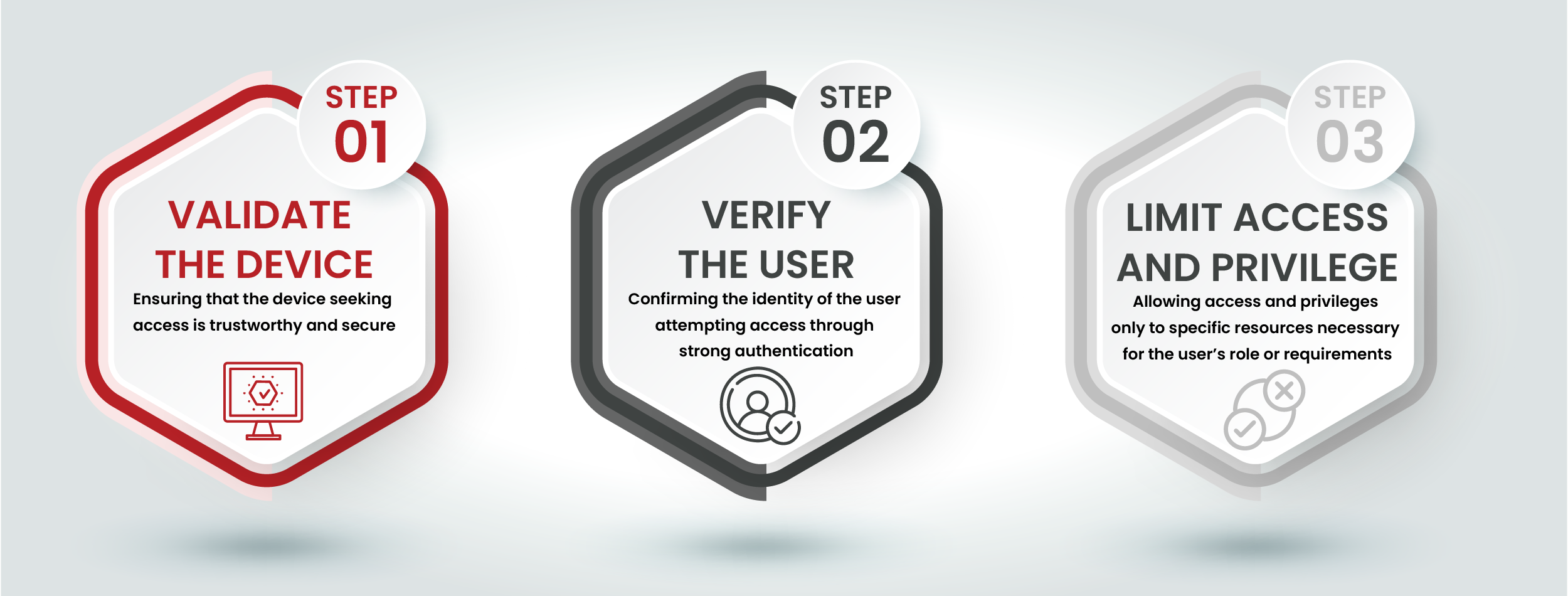
Unlike traditional Virtual Private Networks (VPNs), which often grant unrestricted access to an organisation’s entire Local Area Network (LAN), ZTNA solutions operate on a default-deny principle. This means access is granted only to specific services and resources that a user is explicitly authorised to access.
The core principles of the Zero Trust Model form the foundation of its security framework. They are designed to strengthen security by reducing reliance on trust assumptions and maintaining continuous validation of access:
Users and devices are granted the minimum access required to perform their designated tasks. This approach reduces the potential attack surface and mitigates damage in the event of a breach. Trust is explicitly determined for each access request, rather than relying on predefined roles. This approach protects sensitive financial data and client information from unauthorised access, which is crucial for private equity firms.
To prevent attackers from moving laterally within the network, it is divided into smaller, isolated segments. Even if one segment is compromised, the rest of the network remains secure. This strategy effectively compartmentalises the network, making it difficult for malicious actors to navigate freely. This means that different departments or investment portfolios can be isolated to enhance security.
Zero Trust emphasises real-time monitoring of user and device activities. Any deviations from established norms or suspicious activities trigger immediate action. This ongoing validation ensures that trust is dynamic and can be adjusted or revoked as needed. Continuous monitoring is crucial for detecting and responding to threats that could compromise sensitive financial transactions and client data.
Access control decisions are based on various contextual factors, including user identity, device health, and location. Contextual information plays a pivotal role in making access determinations, enabling organisations to adapt access permissions based on prevailing circumstances, thus minimising risks. This ensures that only authorised personnel can access critical financial systems and data, regardless of where they are working from.
Data is protected through encryption, both at rest and in transit, adding an extra layer of security against unauthorised access. This robust encryption ensures that, even in cases of unauthorised access, the data remains unintelligible to malicious actors, significantly enhancing data security.
These core principles collectively bolster the overarching philosophy of the Zero Trust Model: never trust, always verify. By implementing these principles, private equity firms can enhance their cyber security posture and effectively constantly evolving threat landscape.
Zero Trust Network Access (ZTNA) is a remote access solution rooted in the principles of zero trust. It establishes a robust security framework to facilitate secure user access to enterprise resources. Private applications connect to the ZTNA broker via application gateways. When a user attempts to connect, the cloud-based ZTNA broker verifies the user’s identity and security posture before granting access to authorised applications.
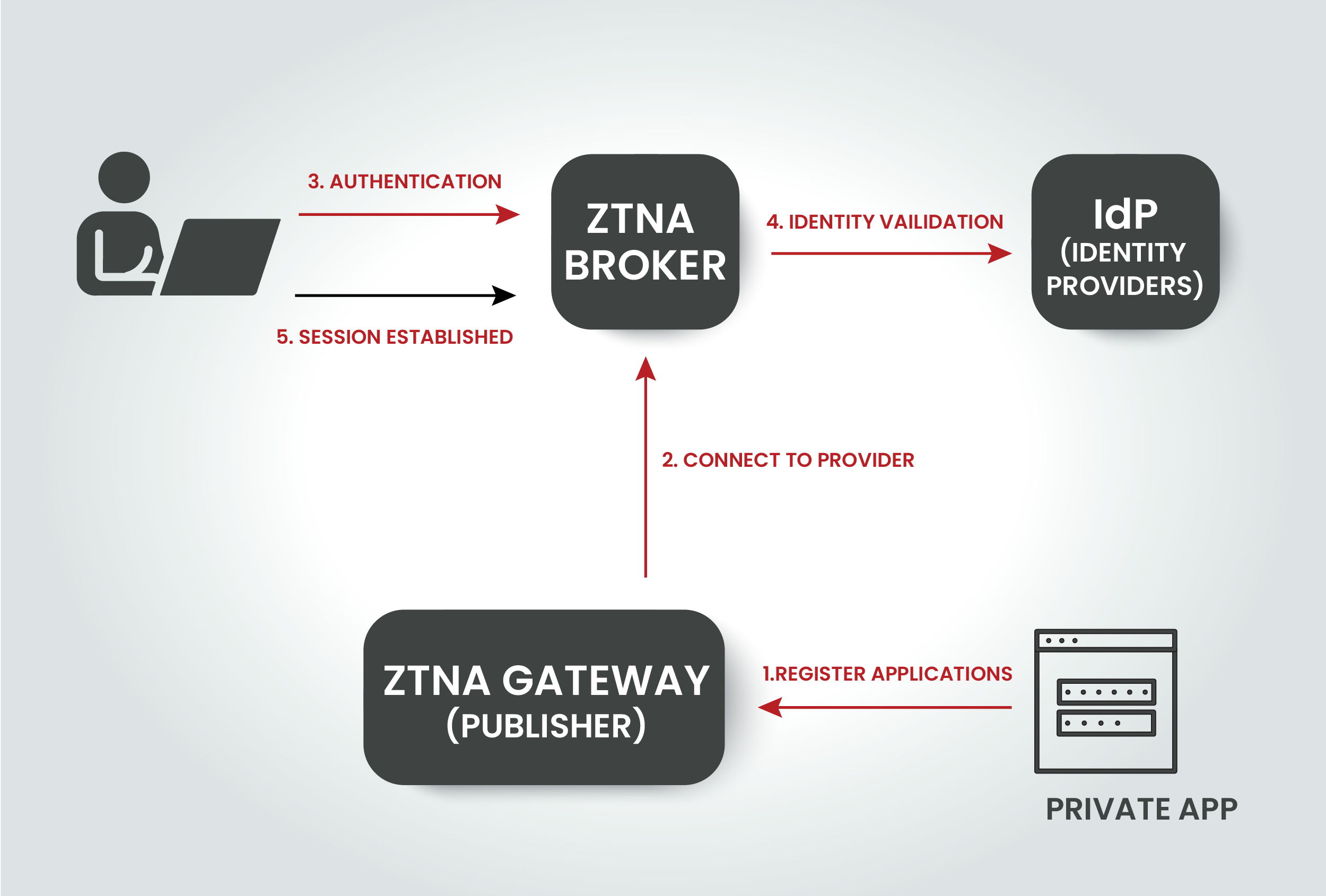
ZTNA ensures that users, regardless of their location or device, have direct access to applications hosted across various environments. This provides a consistent user experience while empowering private equity firms with stringent policy controls. It enables secure, flexible working, essential in the fast-paced financial sector.
Choosing the right cyber security solution is crucial for private equity firms. ZTNA redefines secure access by prioritising identity and context — considering users, devices, locations, and applications. This approach provides the precision and control needed to protect critical resources.
ZTNA secures access not only for employees but also for external partners and contractors. As the financial industry integrates the Internet of Things (IoT) into its networks, ZTNA ensures these new elements do not compromise security.
ZTNA evaluates multiple factors to determine access privileges, granting or denying them with precision. Its flexibility is unparalleled—it can protect resources in data centres, home networks, or public/private clouds. Additionally, it adapts to provide varying access levels based on numerous attributes, seamlessly integrating with your existing identity infrastructure.
Private equity firms are discovering the myriad benefits that the ZTNA model can offer. Here are some of the most compelling reasons to consider making the switch:
Zero trust significantly enhances your security posture by reducing the attack surface. By eliminating the exposure of protocols and services to the public internet, ZTNA acts as a powerful shield against potential threats. In the financial sector, where data breaches can have catastrophic consequences, ZTNA’s ability to reinforce your security defences is invaluable. It ensures that only authorised entities can access your critical assets, minimising the risk of cyberattacks and data breaches.
ZTNA ensures that your data is safe from both external and internal risks. By detecting data usage, monitoring activities, and identifying behavioural anomalies, ZTNA offers comprehensive data protection. It enforces advanced Data Loss Prevention (DLP) rules and policies, ensuring that sensitive financial information remains confidential. Additionally, ZTNA adopts an adaptive access policy based on user risks, making it a formidable defence against insider threats.
Since the onset of the pandemic, many organisations have shifted toward a hybrid or remote workforce model. While many rely on virtual private networks (VPNs) to facilitate this transition, it’s important to recognise that VPNs come with inherent limitations, such as scalability challenges and a lack of integrated security measures.
Traditional VPNs typically provide authenticated users with unrestricted access to the network, which can inadvertently heighten exposure to cyber threats. However, Zero Trust Network Access (ZTNA), especially when seamlessly integrated into a Software-Defined WAN (SD-WAN) or Secure Access Service Edge (SASE) solution, presents an innovative approach to crafting a remote access system. This approach is tailored to limit remote workers’ access to only the resources necessary for their specific roles, effectively enhancing security and minimising potential risks.
In financial services, every second counts. ZTNA ensures that user traffic flows seamlessly and directly to the desired applications. Unlike traditional approaches where user traffic is routed through data centres, leading to potential bottlenecks and slower access times, ZTNA takes the shortest route. This increases productivity by providing fast access to critical data and applications, enabling swift, informed decision-making.
Whether you’re expanding your team, increasing your portfolio, or responding to market shifts, ZTNA offers effortless scalability. By opting for a cloud-based ZTNA service, you gain the agility to adapt your security infrastructure as needed. You can seamlessly scale capacity by leveraging additional licences without the headaches of complex hardware installations or infrastructure overhauls. This flexibility ensures that your cyber security solutions align with your firm’s growth, evolving investments, and security requirements.
Traditional security solutions often involve lengthy deployment processes, potentially leaving vulnerabilities exposed for an extended period. ZTNA bucks this trend by offering rapid deployment. In a matter of days, you can have ZTNA up and running, protecting your critical assets from evolving cyber threats. This swift implementation enhances security and agility, ensuring business continuity and regulatory compliance for your firm.
Private equity firms face unique cyber security challenges that require robust and adaptable solutions. Zero Trust Network Access (ZTNA) provides unparalleled protection. It secures your critical assets, protects your data, and keeps your operations seamless. By adopting ZTNA, you confidently navigate the complexities of cyber security, knowing that your firm is protected against both internal and external threats.
Ready to Simplify Your Cyber Security?
Cyber security is complex. We make it simple. Book a discovery call with our experts today to learn how zero trust can transform your security posture and provide peace of mind. Let us help you protect your investments and ensure the continuity of your operations.
Cyber security shouldn’t be a headache. Get clear and actionable insights delivered straight to your inbox. We make complex threats understandable, empowering you to make informed decisions and protect your business.
Call us +44 20 8126 8620
Email us [email protected]