Building Resilience with DORA: 5 Pillars and Actions for Financial Services
July 15, 2024
The financial services sector faces a constant barrage of evolving cyber threats and digital risks. In response, the European Union (EU) has introduced the ground breaking Digital Operational Resilience Act (DORA). This act establishes a comprehensive framework with five key pillars designed to strengthen the digital defences of financial organisations and their technology partners.
DORA goes beyond simply ticking compliance boxes. It sets clear technical standards for cyber security and digital risk management, aiming to foster a culture of long-term resilience within the financial sector.
This article equips you with the knowledge to conquer the new challenges of financial security. We’ll guide you through the five pillars of DORA, explaining their significance and empowering you with actionable steps to achieve compliance. By the end, you’ll be well on your way to building a more secure digital future for your financial organisation.
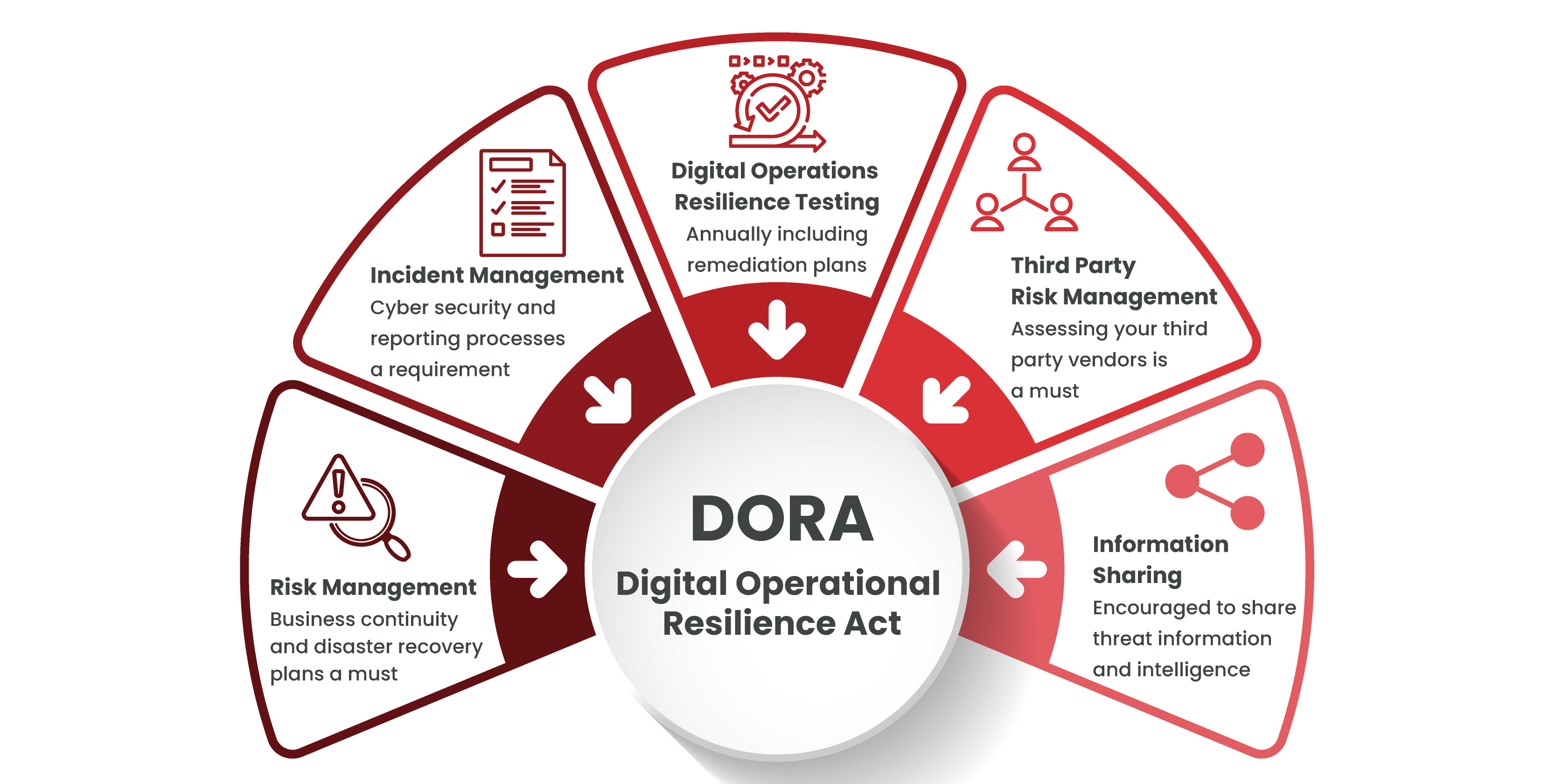
DORA establishes a comprehensive framework built on five critical pillars, each designed to fortify the digital defences of financial organisations. These pillars go beyond mere compliance; they empower businesses to cultivate a long-term culture of resilience against today’s ever-evolving cyber threats.
This pillar forms the foundation of DORA’s mandate. Financial organisations must possess robust frameworks to meticulously identify, assess, and mitigate ICT-related risks. This translates to continuous monitoring of key digital systems, data, and connections.
DORA emphasises a proactive approach. Vulnerabilities shouldn’t be unearthed – they should be anticipated and addressed before they escalate into major incidents. Regular risk assessments, constantly evolving incident response plans, and vigilant monitoring of the ICT environment are crucial steps.
Beyond immediate security benefits, effective ICT Risk Management fosters a culture of risk awareness within an organisation. This heightened awareness translates to a more resilient posture against cyber and digital threats.
The second pillar of DORA focuses on building a robust incident management strategy. This means having clear procedures for swiftly identifying, classifying, and reporting ICT-related incidents. But it goes beyond just reacting to issues.
DORA mandates reporting details like user impact, data loss, and geographical locations. This knowledge-building exercise helps identify trends, understand the evolving threat landscape, and implement preventative measures to minimise future occurrences.
The emphasis is on a well-organised approach. Financial organisations need to:
Transparency is another key aspect of DORA’s incident management pillar. Financial organisations are required to notify relevant stakeholders, including regulatory authorities, about significant incidents. This open communication fosters trust and allows for a collective effort towards strengthening digital operational resilience across the financial sector.
DORA recognises the importance of regularly testing your digital defences to identify and address vulnerabilities before they can be exploited by attackers. This pillar focuses on threat-led penetration testing conducted by qualified third-party vendors. The frequency of testing should be tailored to the risk profile of your assets – higher-risk assets will require more frequent testing.
Here’s what effective testing under DORA entails:
DORA goes beyond simply conducting tests. It requires financial organisations to address the vulnerabilities identified. This means:
DORA recognises that financial organisations rely heavily on third-party vendors. However, these external relationships can introduce vulnerabilities into your digital ecosystem. This pillar focuses on actively managing third-party risk to ensure your entire supply chain contributes to a robust overall security posture.
Here’s what effective third-party risk management under DORA entails:
The final pillar of DORA champions collaboration in the fight against cyber threats. By breaking down information silos and fostering a culture of shared intelligence, financial organisations can collectively strengthen their digital defences.
By actively participating in information sharing, organisations can benefit from a broader understanding of the cyber threat landscape and develop more effective defensive strategies. This collaborative approach fosters a united front against cybercrime, enhancing the digital operational resilience of the entire financial sector.
The five pillars of DORA, as outlined previously, establish a comprehensive framework for financial organisations to fortify their digital defences against ever-evolving cyber threats. Now, let’s translate these pillars into action. Here are five key steps you can take to implement DORA’s requirements and build long-term resilience within your organisation:
The foundation of a secure digital environment lies in a robust risk management framework. Begin by identifying and classifying all potential ICT risks within your organisation, understanding your risk tolerance and potential exposure to cyber threats. Gain a clear view of your critical functions and their dependencies on technology.
Next, consider adopting established ICT governance and control frameworks, such as the NIST Cyber Security Framework. These frameworks provide best practices for managing ICT risks, reducing the likelihood of cyberattacks, and improving incident recovery capabilities. By adopting a structured approach to risk management, you lay the groundwork for building long-term cyber resilience within your organisation.
Efficient incident management is crucial for minimising damage and preventing future occurrences. Review and update your incident reporting standards to align with DORA requirements. Establish robust incident management processes that define clear steps for identification, classification, investigation, containment, eradication, and recovery.
Develop clear communication strategies to keep both internal and external stakeholders informed throughout the incident lifecycle. This ensures timely and coordinated responses that minimise disruption and reputational damage.
Regular penetration testing is essential for proactively identifying vulnerabilities in your digital defences. Develop a comprehensive strategy for conducting threat-led penetration testing by qualified third-party vendors. Tailor, the frequency of testing to your risk profile – higher-risk assets require more frequent testing.
Financial organisations increasingly rely on third-party vendors. However, these external relationships can introduce vulnerabilities into your digital ecosystem. To mitigate these risks, define clear partner strategies and policies for selecting, onboarding, and managing third-party vendors. These policies should establish expectations for cyber security practices and incident response protocols.
Create a comprehensive third-party register that details all vendors, their services, and associated risks. This allows for prioritised due diligence and ongoing compliance tracking. Conduct thorough due diligence on potential third-party vendors, assessing their cyber security posture and adherence to relevant regulations. Regularly perform audits and information security assessments to maintain a clear picture of your third-party risk landscape.
Finally, include robust security clauses in your contracts with third-party vendors. These clauses should clearly outline their responsibilities for data protection, incident reporting, and resilience testing. By holding your vendors accountable for cyber security, you strengthen your overall digital defences.
Collaboration is key in the fight against cybercrime. Actively participate in relevant industry forums focused on cyber threat intelligence sharing. Develop secure channels for sharing cyber security information with other financial institutions and regulatory authorities.
Establish a process for analysing and leveraging the intelligence gained from information sharing initiatives. This could involve threat modelling exercises or updating your incident response plans based on shared knowledge. Finally, fulfil your reporting obligations to the authorities, demonstrating your adherence to DORA regulations.
The escalating cyber threat landscape necessitates robust action. DORA’s arrival provides a vital framework for financial organisations to strengthen their digital defences across the EU.
Compliance requires proactive steps: refining risk management, building incident response processes, conducting regular testing, managing third-party risk, and fostering information sharing. While investments in governance and addressing vulnerabilities are needed, the benefits are clear: enhanced operational resilience and a competitive edge in a security-conscious market.
Explore our resources for further guidance:
Cyber security shouldn’t be a headache. Get clear and actionable insights delivered straight to your inbox. We make complex threats understandable, empowering you to make informed decisions and protect your business.
Call us +44 20 8126 8620
Email us [email protected]